Weird smeared transactions in Trezor wallet. What is this? Wallet hacked?
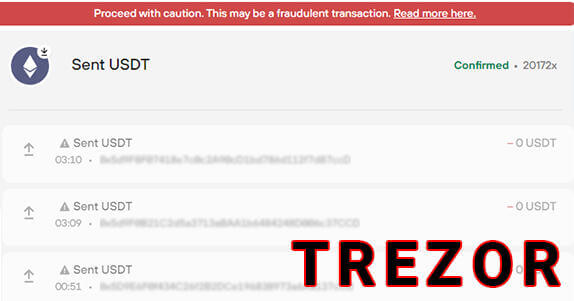
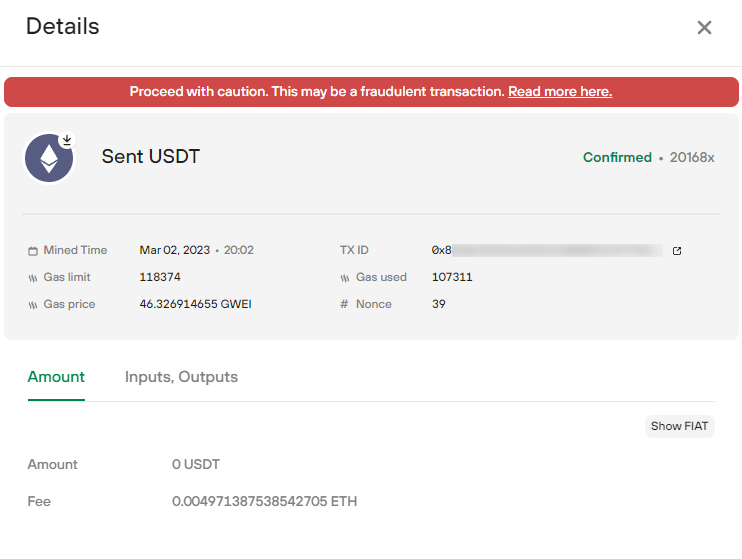
Proceed with caution. This may be a fraudulent transaction: What's it?
Transactions of this type have appeared in your Trezor wallet:
«Proceed with caution. This may be a fraudulent transaction.»
Don't worry, your wallet hasn't been hacked! Later in the article we will explain what these transactions are and what to do with them?
The official answer to this problem is on the website Trezor.
Strange smeared (blurred) transactions in the Trezor wallet that you did not make
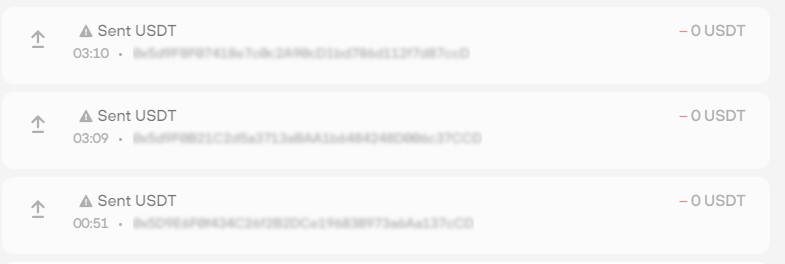
Recently, such transactions have begun to appear in the Trezor wallet, which look as if they were covered up:
If you open this transaction, you will see the following:
«Proceed with caution. This may be a fraudulent transaction.»
This is indeed a fraudulent transaction, but nothing has been stolen from your wallet, you have not been hacked, your private key is safe!
Why do strange transactions appear in Trezor?
As we have already said, these are fraudulent transactions, they appear when a fraudster tracks down your wallet, in the hope that you will then send your cryptocurrency to his address by mistake.
How does it work? You have made a transaction to some address, for example, here:
«0x5t2F2FEr0440A149eD3s4218B86b18Cc11123dWe»
In your wallet, in just a couple of minutes, a transaction appears, the wallet of which looks like this:
«0x5t2F2Ftr0440A231eD3s4118B84b16Ce11123dWe»
As you can see, the beginning and end of the wallet are identical, the differences are only in the middle.
Scammers create specially similar wallets (the same beginning and the same end) so that the next time the user makes a transaction, he mistakenly sent funds to the fraudster.
Simply put, an attacker creates a "personal address" that can be configured with a certain set of characters, thereby it becomes similar to the address of the intended recipient.
When a victim carelessly copies an address from a previous transaction, they may instead accidentally send their assets to a fraudulent address.
Let's take a closer look at this next.
Who can fall for such tricks of scammers?
Let's imagine that user "A" wants to send funds from his Trezor wallet to his account in the Huobi exchange.
For the first time, he enters the Huobi exchange and receives there the ERC-20 address of the coin he needs, for example, USDT.
Then he goes to his Trezor wallet and transfers USDT coins to his account at the exchange.
After a couple of days, weeks, the user wants to send a couple more coins to his account in the exchange. But this time he goes directly to his wallet and makes a transfer from history, to the last address. In this case, the coins go immediately to the fraudster, since the last address in the history will be the same fraudulent one (which has the same beginning and end of the address).
Option 2, after a couple of days, weeks, the user enters his Huobi exchange and opens his Trezor wallet for a new coin transfer.
The user looks (on the Huobi exchange) at which last 4-5 digits and letters his digital wallet ends and finds it in the history of Trezor. After that, the user transfers coins to this wallet. Since the last one was a fraudulent transaction, the user will transfer his funds to a similar address (the digital wallet looks identical at the beginning and at the end) and loses his coins!
How not to fall for the tricks of scammers in Trezor?
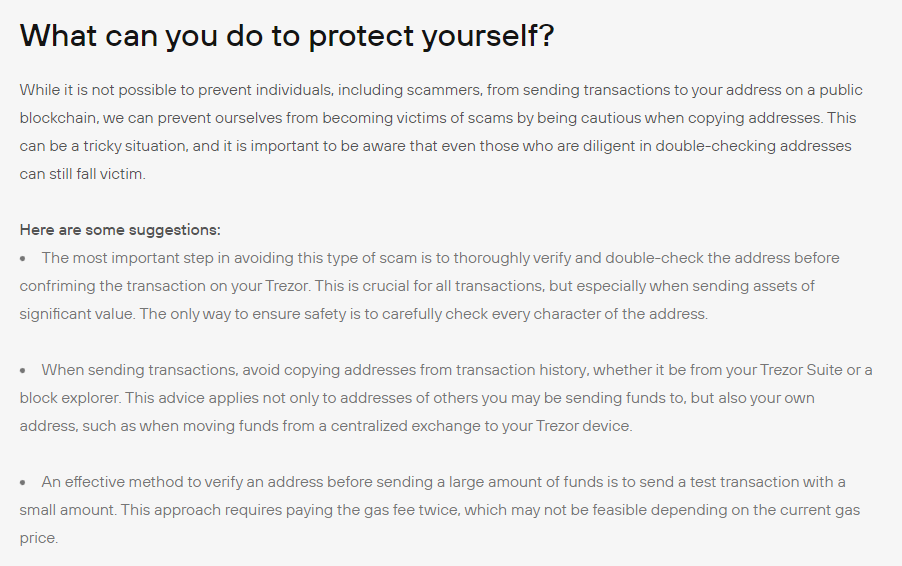
Never send coins to an address from history! Do not be lazy and spend a couple of seconds of your time and copy the address you need from the exchange, another wallet, and so on!
Due to the fact that such fraud has become more frequent, it is not safe to use the address history!
Trezor himself is aware of this problem and writes the following about it:
How do scammers do this?
They do this by sending transfers of 0 BUSD, ETH, USDT, etc. from a fraudulent address to a wallet address, as well as sending transfers of 0 BUSD (etc. coins) from the wallet address to the address of scammers.
You might think that they can't send anything from the wallet address to their fraudulent address because they don't control the wallet's private keys, but that's not entirely true.
The ERC20/BEP20 token transferFrom method allows any address to send funds from any other address if the amount does not exceed the specified norm, but in this case, since the amount is 0, it does not exceed the allowable amount, which by default is 0.
So now the scammers just hope that when this wallet owner wants to make a deposit to his exchange address (another wallet, etc.) next time, users will be too lazy to log into their exchange account to copy the address from there, and instead copy it from their recent transaction history (where they will copy wrong address because it looks familiar).
And even if users check the address on the exchange's website or on their phone to make sure that the first 5 and last 5 characters match the address they copied, everything "will be fine", users will think, and confirm the transfer to the address of the fraudster.